IoT security can be approached in multiple ways. Different underlying hardware, firmware, and software are all available to enable devices to be built with the right level of security for a particular use case. This also enables differentiation, with some products warranting more robust security than others.
PSA Certified believes that security is pivotal to the connected world and encourages security to be embraced by new areas of the ecosystem. Below we explore the evolution of the SIM as a trusted component in IoT devices along with how this new application uses the PSA Functional APIs in a new way to make the world a more secure place.
Building the Foundations of Trust
Despite the need for product differentiation, there should be one constant. Every IoT device should be built on a foundation of security, a secure hardware element playing the role of a Root of Trust (RoT). The RoT holds security functions, secret keys and information about the device, and securely stores information and data from device applications.
Securely Communicating RoT Secrets
For applications, cloud providers and those further up the value chain to be able to trust the data from the RoT, a consistent and secure mechanism to communicate with the RoT is required. This needs to be effective regardless of the underlying hardware and RoT, allowing one solution to be used for the whole of the value chain.
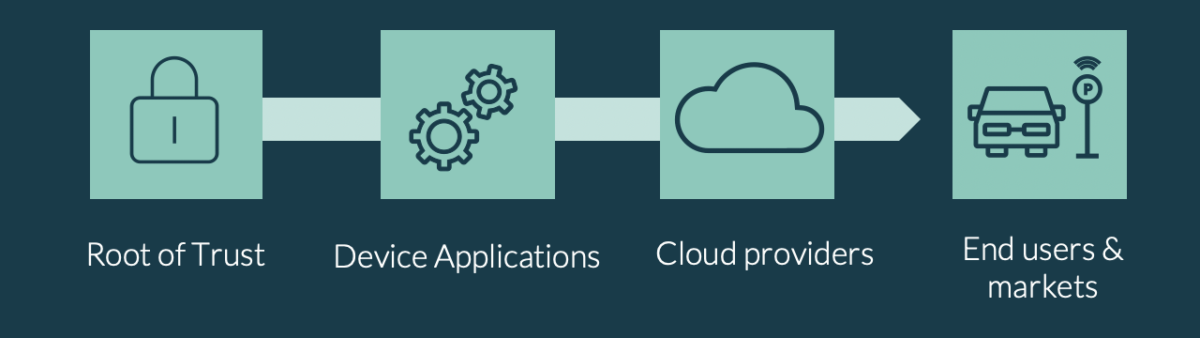
SIM as a RoT
The SIM, being the worlds most deployed secure element, is a tried-and-tested platform with advanced security and cryptographic features. Mobile devices first use the SIM card to identify and authenticate the user as a subscriber of a given mobile network service, the result of which is used to secure the physical, over-the-air radio signals. It is ubiquitous in devices and provides a secure place for the storage, provisioning and use of security credentials. It also enables interoperability across vendors and device makers.
Additional to its history, traditional SIMs have evolved, with the emergence of the eSIM and new technologies in progress, the SIM becomes an increasingly feasible RoT solution for size-constrained devices.
With this, companies are developing innovative solutions to lower barriers and make the use of SIM in IoT a seamless experience.
IoT SAFE project: Leveraging Chip-to-cloud Security with SIM Technology
Today, devices like laptops equipped with web browsers automatically open a secure HTTPS connection when users visit secure sites. The underlying technology that enables private and safe communication between the user and the website is TLS (Transport layer security).
Similarly, IoT devices need to send data through a secure connection to the cloud, so that same level of security is required. These devices, however, typically lack the components required to achieve a secure connection.
IoT SAFE was an initiative of the GSMA and developed by wireless security thought-leaders to introduce industry guidelines to help secure traffic between IoT devices and the cloud and leverage the SIM as a scalable and standardized hardware RoT. The IoT SAFE application outlines a common interface and uniform method of using SIM for authentication between the application and the cloud and highlights best practice to achieve this. It enables this connection by using the same type of TLS (or DTLS for UDP sessions) to secure the end-to-end connection going from the application running in the device to the cloud. This is achieved by leveraging the SIM card, which is currently used for mobile network authentication, to act as a safe deposit box for additional security credentials that manage the identification and authentication of the device to the cloud.
Until recently, operators have been reluctant to provide access to the SIM due to its importance in protecting network authentication credentials. But that’s changing; the world is acknowledging that if IoT is to be successful, security must be baked in from conception.
The IoT SAFE application outlines a common interface and uniform method of using SIM for authentication between the application and the cloud and highlights best practice to achieve this.
IoT SAFE Guidelines Endorse PSA Functional APIs
Within this best practice, IoT SAFE specifically highlights the PSA Cryptography API as the de-facto way to bridge security features within the SIM with the device application. The result? Software platforms and applications can easily access security features without the need to develop these notoriously difficult APIs themselves or coding hexadecimal SIM commands (known as APDUs) wrapped in AT commands to pass through the modem interface. These standardized APIs enable quick application development with assured use of the APIs.
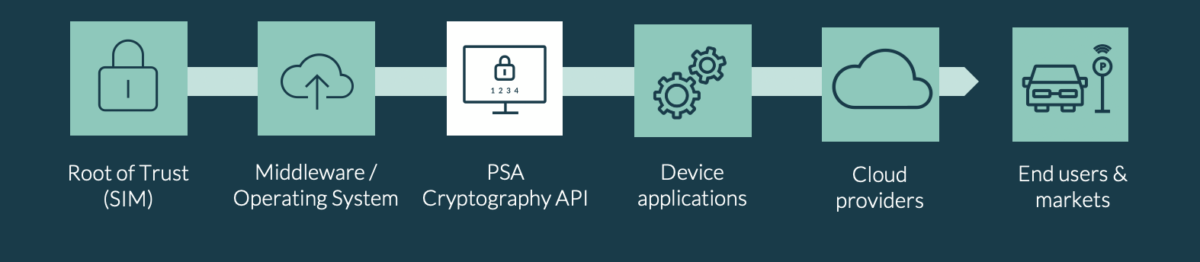
PSA Functional APIs are Leading the Way for IoT Security
The IoT SAFE API recommendation is the first, very important step towards a more standardized way of building security into IoT.
By leveraging the PSA Functional APIs, device manufacturers and service providers will find it easier than ever to securely establish connections with devices that protect IoT data, while also simplifying the process of provisioning and lifecycle management for millions of IoT devices.
The PSA Functional APIs have been developed to be easy to implement regardless of the underlying hardware, software, application or cloud to create a standardized function across the IoT.
PSA Certified offers these free APIs, an API test suite and corresponding certification so that application developers and cloud providers can focus on their product knowing that the RoT is in place and communication is secure using the APIs.
Next Steps
The PSA Functional APIs lower the barrier to security. Learn more about the APIs and Functional API Certification.
