IoT Security for the Remote Healthcare Market
The following article is written by our partners at Flex as part of our In conversation with … series.
Technology has played an increasingly important role in our lives over the past 18 months, and that includes enabling us to continue to access health care. Throughout the COVID-19 pandemic, advice that would usually be offered in-person was instead provided during virtual consultations. The increase of connected devices gathering data, enabled doctors to monitor or even treat some health conditions remotely.
Despite the sector’s rapid transformation, the potential of the remote healthcare market is still to be realized. A report by Grand View Research, Inc. predicts it will grow from about $8 billion to just under $24 billion in the next seven years. The Internet of Things (IoT) could power that expansion.
However, it’s clear that there is a lot at stake. Original equipment manufacturers (OEMs) that want to seize the opportunity are taking small and slow steps to ensure the rollout of connected healthcare doesn’t cause a ripple effect of avoidable hacks. With this in mind they must develop smart and secure devices to ensure people can confidently benefit from innovation.

The Importance of IoT Security in Healthcare
So, what do we mean by ‘secure’?
When we talk about the security of IoT products, we usually focus on protecting information confidentiality, integrity, and availability. In a healthcare setting, we have another even weightier responsibility – keeping people safe. If we are connecting equipment such as a portable ECG recorder, infusion pump, or blood glucose monitor to the internet, we must ensure they can be trusted. That is because the equipment is gathering data that healthcare professionals will use to make important clinical decisions.
Several years ago, researchers highlighted the importance of protecting IoT products by demonstrating that a cyberattack on a potentially life-saving device was possible when there was a weakness in its security. For example:
- Sensitive patient information may be disclosed during a data breach.
- A denial-of-service attack might prevent someone from using a device or deplete the product’s battery, or even prevent data from being sent to the clinician.
- If non-genuine software is executed on a device, it could lead to incorrect diagnosis or treatment.
There could also be implications for the organizations involved in the development of the IoT device and for the institutions providing the healthcare. Their reputation, continuity of service and revenue could be impacted by a cyberattack and trust could be eroded.
How Security Impacts the Development and Deployment of IoT Devices
The challenge for OEMs is that building a trustworthy IoT device takes time, but customers and investors want to help people benefit from the technology now. Quick prototyping is essential for manufacturers because it speeds up the development process, reduces costs and decreases time-to-market.
However, selecting the optimal combination of trusted components, including sensors and connectivity, requires extensive investment in scouting and developing a network of silicon providers. To remain cost effective, security must be built-in to a device from the silicon up – in line with industry best practice. There are also a growing number of security requirements that must be met if manufacturers are to comply with major government guidelines and legislation.
When you factor in these variables, it becomes clear that designing security into a device can be complex and time consuming. The good news is the ecosystem can help.
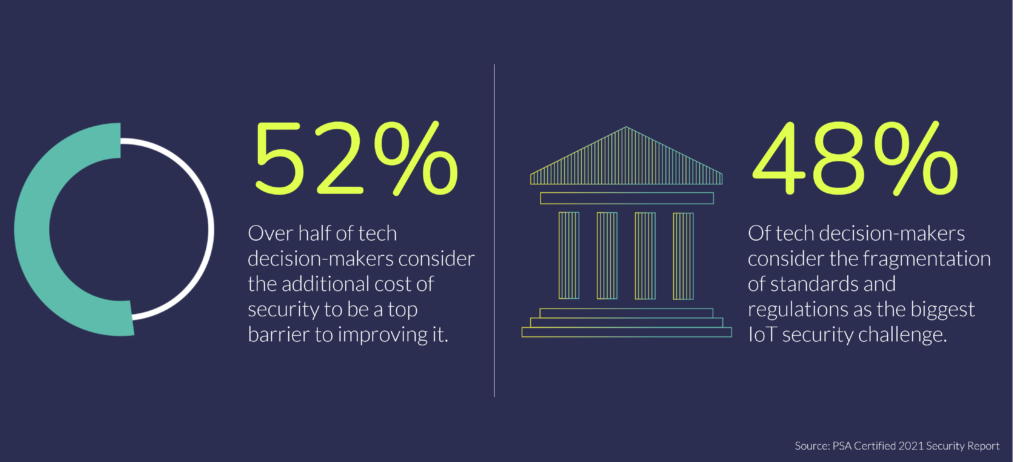
Tackling Key IoT Security Challenges
Here at Flex, we developed our Sensor Integration Platform to help our healthcare customers overcome these challenges and bring potentially life changing IoT products to the people who need them. The modular platform enables customers to streamline development while maintaining security, and offers more than 40 hardware and software building blocks that can be ported into any product architecture with minimal intervention.
This empowers Flex customers, who are often companies focused on pharmaceuticals and diagnostics, to innovate. They can visualize and test ideas on a real product architecture to understand the opportunities and limitations prior to investing in further development. Our design-led manufacturing expertise and ready-to-import design files, together with tested embedded software and built-in security give our customers a competitive advantage: time-to-market is improved, development costs are reduced, and fundamental security principles are addressed.
In order to put our hardware to the test, we developed a reference application specifically for the remote healthcare market. The ECG signal from a patient is transmitted in real-time to an online dashboard, where it can be accessed and visualized by a physician. In future, it could even be linked to a patient’s health records. This makes the delivery of health care more efficient and precise. In addition, recent studies show some patients prefer this type of remote healthcare over in-person visits and want to be more aware of their health without always having to seek assistance in a clinical environment.
Establishing a Foundation of Security
A patient and care giver must be able to rely on the data that is being gathered by the IoT device. A typical effective design guideline is to segregate the design team from the validation team as two separate entities. This allows a deeper, more structured and reliable product evaluation. This is even more important when we talk about validation of critical functions to enable the device’s security goals. This is the reason we used the PSA Certified framework and certification scheme for our Sensor Integration Platform. We wanted our customers to have peace of mind based on an external and recognized authority.
We carefully selected pre-verified, PSA Certified Level 1 STM32L4 from STMicroelectronics (based on the Arm Cortex-M4) and PSA Certified Level 1 FreeRTOS system software so we could offer our customers, especially companies that have no cybersecurity expertise in-house, the tools and know-how to design security into their device and navigate the changing regulatory environment. We then asked independent labs to assess our development platform against baseline security requirements and industry best practice. The PSA Certified status we were awarded assures our customers that their products are being built on a strong foundation of security, that is, a Root of Trust, and they will be compliant with the major standards and regulations driving cybersecurity for connected devices – NIST 8259A and ETSI EN 303 645. In doing so, we are also helping our customers ensure they do not lose access to important markets because they have overlooked the relevant legislation.
The path to certification was clear and the stamp of approval it gives us, which our customers can then capitalize on, is an added benefit.

The Future of the IoT in Remote Healthcare Market
As the market continues to grow and remote patient monitoring becomes mainstream, hackers’ interest in the sector will grow alongside it. Our role in the industry is to build people’s trust in innovative connected devices because this will be fundamental to the acceptance of new technologies. Emerging regulations and baseline requirements are changing the way we see security, and this is helping us ensure the benefits of remote healthcare devices do not come at the expense of patients’ privacy or safety. We also believe the PSA Certified framework, independent assurance program and certified solutions such as our Sensor Integration Platform take us a significant step towards meeting that goal.
Visit our website to learn more about our development platforms.

Building Trust in Internet of Medical Things (IoMT) Devices
In a healthcare setting, it is critical that products are built on a Root of Trust. In this PDF overview, Flex provides insights into their vulnerability management process using the PSA Certified Level 1 Sensor Integration Platform, Flexino. They illustrate how the use of an ecosystem of certified system software and silicon chips can help navigate the complexity of designing security into a device.
