Connected devices are deployed in homes, businesses, industries, and in towns and cities. Some gather and analyze vital information, others perform less critical functions, but they all have the same value-adding feature – connectivity. Interest in connected devices continues to grow and so do the cybersecurity risks. In our annual survey of technology decision makers, we found that security is a top priority for most businesses, and that investment in security has increased to meet legislators’ and customers’ concerns about the vulnerability of connected products.
However, securing a device is complex, and in the early days of the connected consumer products, many companies struggled to build security into their connected products. Expert help was not always at hand, and if it was available, securing a device was still costly and time consuming. As a result, security was often added as an after-thought or even completely overlooked if budgets or deadlines were stretched.
Since then, we’ve learned that security isn’t the responsibility of a single company and the only way to secure a device is through collaboration. We established PSA Certified as a way of uniting the ecosystem so everyone can play their part in building a more secure future. The scheme draws on the expertise of 11 leading security companies and provides a simple, four-step framework and free, standardized resources that make securing a device easier, quicker, and more cost-effective than in the past.
Establishing Trust in Connected Devices
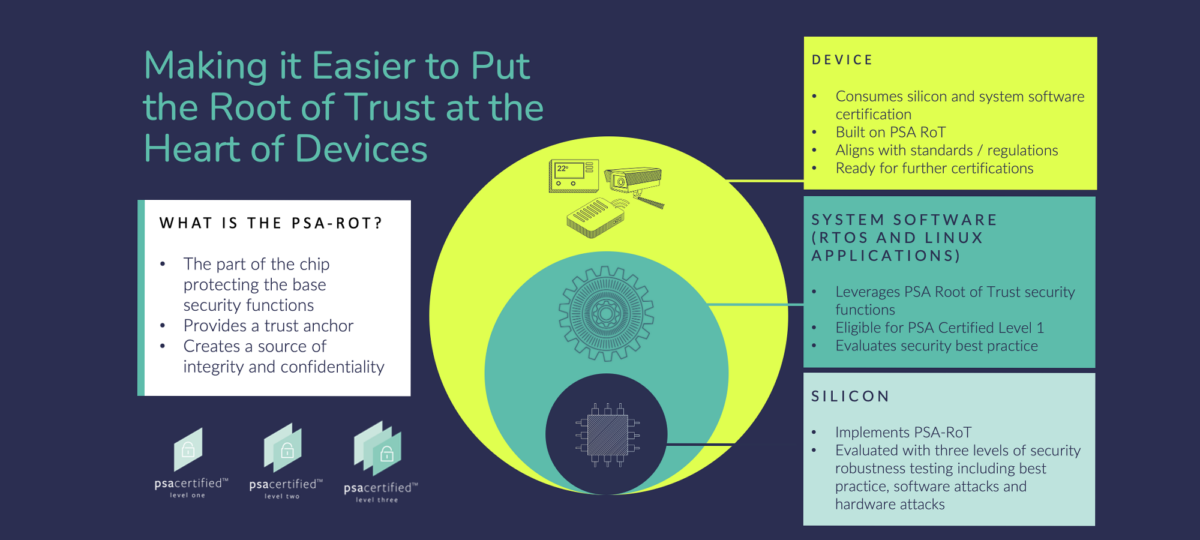
At the heart of our approach is starting the security journey at the silicon with a Root of Trust (RoT). A RoT establishes a secure foundation that the system can rely on. It’s the part of the chip that essential, trusted functions such as attestation, secure boot, cryptography, and secure storage are carried out on. The complexity of these functions is usually hidden by an interface that enables software developers, who may not be security experts, to utilize them.
Most of the world’s leading silicon vendors are implementing the PSA Root of Trust (PSA-RoT), which was developed specifically for the modern connected devices. It’s an easy to use and cost-effective solution, which means security can be built-in to any device, including low-cost microcontrollers.
Building Assurance Throughout the Supply Chain
Supply chains continue to be vast and fragmented, which can make understanding the security credentials of a single device, designed by multiple partners, a challenge. PSA Certified is built with composition in mind: there are three levels main levels of PSA Certified certification. Each level confirms a level of security robustness and the requirements for companies increase as they move from levels one to three.
Certifications are consumable, which means that software developers and device manufacturers that build on certified components can benefit from a vendor’s commitment to security and offer their own customers assurance. The certification can also be used with other security frameworks and evaluation schemes.
In this way, we’re leveraging the expertise of the ecosystem and providing evidence that shows security has been built into a device from the ground up. We’re also establishing a common language for the industry, so we know we’re all working to the same security requirements.
We think of it as being like layers of an onion. If silicon vendors build on an independently tested RoT, software developers know they’re working with secure hardware, and device manufacturers have confidence in the security of the components they choose for their end products.
The Ecosystem is Expanding
There’s widespread support for this layered approach to security. In less than five years, PSA Certified has grown to include more than 80 leading companies and almost 200 certified products that are available for partners to build on.
The next step for the partnership is to step up our support for the industry as it navigates the cybersecurity laws and baseline security requirements that are being introduced to protect consumers around the world from cyberattacks. In the UK and Europe, companies should be considering how they will comply with the following key legislation:
- In the UK, the Product Security and Telecommunications Infrastructure Act (PSTI)
- The EU’s Cyber Resilience Act and Radio Equipment Directive (RED)
Meanwhile, the US has introduced its voluntary U.S. Cyber Trust Mark, a labeling scheme for consumer devices. The requirements for the Trust Mark are currently being developed but they’re expected to be based on the existing National Institute
of Standards and Technology (NIST) cybersecurity baseline standards.
PSA Certified Level 1 is aligned with NIST 8259 and Europe’s EN 303 645 cybersecurity standards and is reviewed annually to ensure it evolves as the regulatory landscape changes. Our most recent update will be particularly useful for companies that are preparing for the new legislation.
You can find detailed advice on meeting security requirements with PSA Certified Level 1 in our recent blog or learn more about the emerging legislation in our white paper.
In the above video, two PSA Certified founding members summarize our approach to security and highlight the benefits of collaboration.

