This blog was written by Riscure as part of our ‘In Conversation With…’ series. Riscure is one of the seven co-founders of PSA Certified and one of the approved PSA Certified evaluation labs.
As the IoT realm has developed at incredible rates, there has come to be a lot at stake. Today, we explore why IoT security is so important and the critical baseline level of security needed to establish a device security.
PSA Certified, The Breakdown
When we leave the house, we check for the three essential items: phone, wallet, and keys. However, this simple checklist has transformed at a rapid pace as modern tech has evolved over the past decade.
Whether it’s your smartphone, digital wallet, or remote car key fob, there now exists a level of unprecedented risk in the industry. In fact, unauthorized use, data loss, or system malfunctioning introduces opportunities to compromise components of a system, from simple data to entire infrastructures.
Intended to create an architectural foundation, rather than fix-all solution, PSA Certified was crafted by the industry to amplify security efforts. At Riscure, we’re proud to be a co-founder and evaluation laboratory for PSA Certified. After decades of embedded device evaluations in domains such as premium content, mobile payment, defense, and more, we’re well-versed in not only the commonly made mistakes, but up-and-coming vulnerabilities too.
As our analysts continue to invest in new attack methods, Riscure is provided with the expertise to constantly improve our evaluations, which translates to more secure systems for all. With insight into the minds of modern day hackers, we empower your product to be one step ahead, so you don’t fall behind. The result? Confidence for you and your customers.

The Vulnerabilities
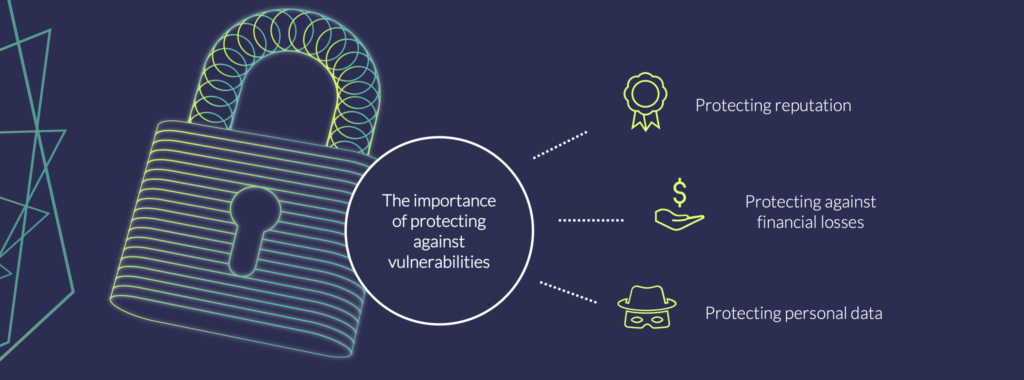
As mentioned, in today’s increasingly connected world there is a lot at stake; for users, who don’t want to get their personal data to become public, and for development companies, who cannot afford a damaged reputation or financial losses as a result of significant security incidents. Hence, it’s crucial for IoT product developers to think carefully about the assets they want to protect, as well as the types of threats in the market. These considerations provide the foundation for not only a security strategy, but also help determine which preemptive measures to take.
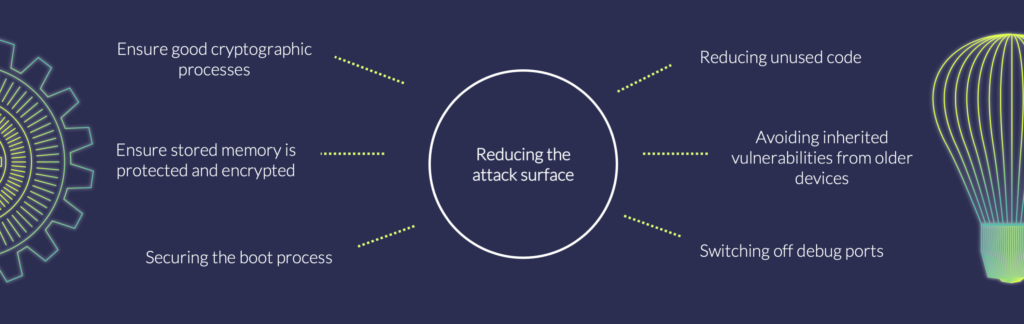
Yet, even the most inventive technical countermeasures can be easily undermined if simple security development rules are not followed. One rule is that of reducing the attack surface as much as possible. As an example, we often see the habit of reusing code from other device implementations without removing unused pieces. With that, he or she not only inherits old vulnerabilities, but also poses the opportunities for novel ones. And this is just one example.
The Countermeasures
When tasked with the reduction of an attack surface, a developer should first remove access to the device’s debug port. From there, ensure that the boot process is constructed such that it cannot be interfered with.
Then, it is vital to make sure that data stored in memory is protected. One avenue of protection would be to encrypt all data that is stored in flash memory, in order to prevent intellectual property theft or leakage of cryptographic key material. A different type of measure is to physically hide the access to a flash memory component, reducing the potential for attackers to directly tap such interfaces. Even better, developers could implement embedded memory rather than an external flash. While cryptographic keys require additional attention to secure, this measure further combats potential vulnerabilities that could sacrifice your system.
For embedded device development teams, especially those where security expertise is limited, it can be challenging to effectively address all of the above. PSA Certified is helping to streamline this process, but it’s sadly still a step that’s often left to the end of a development lifecycle. As developers, we need to recognize the value of device security considerations throughout the course of the entire development lifecycle. The result? A secure development lifecycle for you and your customers.
Want to dig deeper? I recently co-hosted a webinar with Jim Carver, the Strategic Business Development Manager at Arm to address this exact topic. Tune in here, as Jim and myself delve deeper into PSA Certified, the IoT space, and more.
