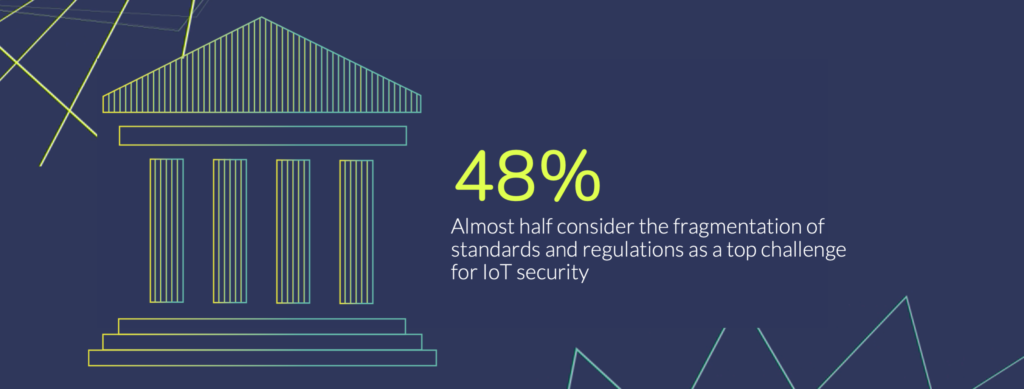
In the PSA Certified 2021 IoT Security Report , 48% of respondents cited standards and regulation fragmentation as a top challenge for IoT security. As the world wakes up to the burden of insecurity, we are seeing a growing number of standards and guidelines. This mountain of requirements is slowing down the adoption of technology, as many developers are adopting a “wait and see” approach, waiting for regulations to establish before evaluating the robustness of their products.
In this blog, we explore how PSA Certified is reducing fragmentation of security standards in the IoT ecosystem, why the PSA Root of Trust is so important, and how a choice of evaluation methodologies can help the chip developer.
Enabling Certification Reuse
Over time, the guidelines for specific markets will become requirements, and in some cases, they will develop into vertical market-specific certifications (for example industrial, medical and consumer). If we’re not careful this rapid growth of varying requirements will exacerbate the fragmentation problem, slow down the market and stifle innovation. Therefore, it’s critically important that we encourage certifications that can be reused across different schemes and support composite evaluations (where certifications can be more easily reused later). By making use of these two approaches, we can ensure that all products are aligning to a common security language and reuse drives efficiency for the value chain when complying with additional market requirements. By enabling this composite and reusability approach, which can be utilized in multiple verticals we reduce fragmentation and ensure that security remains the number one priority.
PSA Certified Level 1 is a security questionnaire with a lab audit; the questionnaire has three sections that work in composition: Chip, System Software and Device. This makes it simpler for OEMs to fill in the Device section if they are using chips or software platforms that are already PSA Certified. Silicon vendors can certify at higher PSA Certified levels to showcase additional robustness to OEMs.
A PSA Certified Level 2 chip has a security promise of protecting against scalable software attacks whereas a PSA Certified Level 3 chip offers protection against substantial physical and software attacks. Chips being evaluated at PSA Certified Level 2 or PSA Certified Level 3 are subjected to penetration testing in an evaluation lab, which means an Evaluation Methodology (EM) needs to be selected by the developer. PSA Certified offers a choice of two equivalent evaluation methodologies for Level 2 and 3: an in-house CSPN style EM and GlobalPlatform’s SESIP (Security Evaluation Scheme for IoT Products).
Aligning to a Common Approach for Security
A common approach is key to unlocking the certification reuse that we mentioned before. At the inception of PSA Certified over two years ago, we defined a new chip-based security component, the PSA Root of Trust (PSA-RoT) and created an independent security evaluation and certification program to assess security implementations according to a Protection Profile for the PSA-RoT. Wide adoption across the market has resulted in over 60 PSA Certified products from silicon providers, software vendors and OEMs who are all aligning to the same security goals. This enables device manufacturers to leverage the security functions from the silicon RoT and use the PSA-RoT as a foundation for further device certifications.
The PSA-RoT is a security component that is isolated in a Secure Processing Environment and acts as the trust anchor for the device and services that depend upon the device. It is usually created by combining trusted hardware (such as cryptographic accelerators, private key stores and random number generators) with trusted firmware that is hidden from the main device software by a hardware isolation mechanism. It provides a small set of security primitives (such as crypto, secure storage, attestation and secure boot) which lay the foundations of device security and must be trusted by the device and services. Consequently, the PSA-RoT must be dependable across the value chain, and an independent test lab-based evaluation helps to build trust. The chip’s PSA-RoT can be tested through a PSA Certified security evaluation where there are three levels of progressively increasing assurance and robustness for silicon vendors.
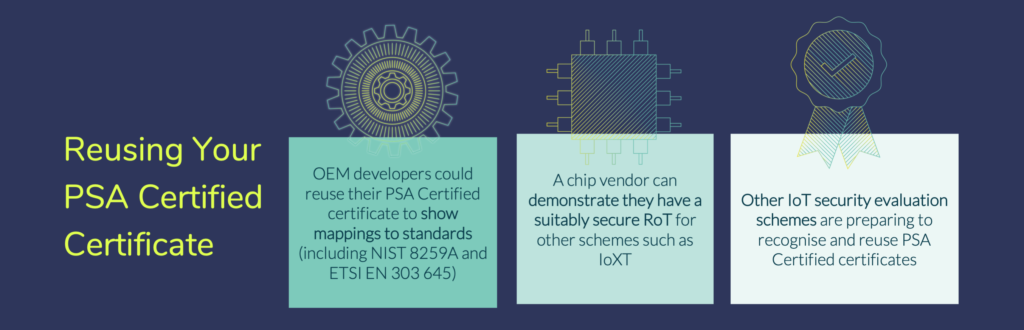
The developer’s investment in achieving PSA Certified status can often be reused by other security frameworks and evaluation schemes:
- OEM developers could reuse their PSA Certified certificate to show mappings for NIST 8259A cybersecurity baseline requirements or device parts of EN 303 645.
- A chip vendor can demonstrate they have a suitably secure RoT for other schemes such as IoXT.
- Other IoT security evaluation schemes (soon to be announced) are preparing to recognise and reuse PSA Certified certificates.
Protection Profiles and Evaluation Methodologies Explained
Another key area for creating consistency in IoT is with Protection Profiles (PP) and Evaluation Methodologies (EM). The relationship between the two can be confusing if you are new to certification as the way the PP is written will depend on the choice of EM.
- What is a Protection Profile (PP)? A protection profile defines the security problem for the “thing” (otherwise known as the security target) that an evaluation lab will test via vulnerability analysis and penetration testing. PPs list the base security requirements that the evaluation lab will test. The PP is architecture and implementation-independent giving the developer freedom to fulfil the security requirements in different ways. For example, the PSA Certified PPs define what needs to be tested for PSA Certified Level 2 (secure storage, secure boot, crypto etc) and adds additional requirements for PSA Certified Level 3. The PSA Certified certification level also sets the number of days of lab testing, whether source code is required from the developer, or if physical attacks are in scope in the evaluation. In general, PPs can be written in plain English (lightweight PP), a semi-formal approach such as Security Evaluation Standard for IoT Platforms (SESIP) or use a formal Common Criteria (CC) style. Learn more about the relationship between PSA Certified and CC here.
- What is an evaluation methodology? The Evaluation Methodology (EM) informs the developer and the evaluation lab how the testing should proceed.
Choosing a certification scheme often means that the PP (and in turn the EM) is fixed for you and restricts your choices when it comes to certification reuse. However, PSA Certified is different as we are fostering alignment across the industry and have developed two equivalent PPs for the PSA-RoT. PSA Certified offer two PPs that enable chip vendors to choose either one written in the style of a Certification de Sécurité de Premier Niveau (CSPN) PP or a GlobalPlatform SESIP Profile for PSA Certified Level 2 or PSA Certified Level 3.
What is the Relationship Between PSA Certified and SESIP?
The PSA Certified founding members (otherwise known as the PSA JSA) believe that developers should have a choice of evaluation methodology. The two routes have equivalent security robustness and assurance, managed under one Certification Body (CB) and lead to the same PSA Certified level. An option to use SESIP EM has recently been added as an alternative to the existing CSPN-style EM for PSA Certified Level 2 and PSA Certified Level 3. SESIP follows the mandatory aspects of the Common Criteria standard but offers greater ease of use and a custom set of assurance levels that have been aligned with PSA Certified.

SESIP or CSPN-style? Choosing Your Certification Methodology
With the addition that silicon vendors can now achieve PSA Certified Level 2 and PSA Certified Level 3 using either the CSPN-style methodology or GlobalPlatform’s SESIP EM, you might be wondering which to choose.
| SESIP | CSPN-style |
| Uses a more formal documentation style with a library of Security Functional Requirements (SFRs) that the PP references. The PP typically requires more study than a CSPN-style PP to interpret its meaning and implication for the developer. OEM’s might want to develop their own market-specific SESIP Profiles. If the chip vendor has a SESIP evaluation it will be easier for the OEM to use this certificate in composition, which means the OEM can reuse it and reduce their efforts and costs. | The key benefit of the CSPN PP is that it’s written in plain English and is, therefore, easier for the developer to interpret. CSPN is a logical choice for companies that are new to certification and do not have first-hand experience in writing a formal security target document. CSPN saves time and energy involved in learning formal CC requirement language and easier documentation. Some of the PSA Certified documentation only available in CSPN-style, this includes PSA Certified Level 2 Ready, which is a pre-certification evaluation for components that can’t reach all of the requirements needed for the full certification process. |
Composite Certification: Unlocking New Potential and Easing Fragmentation
In conclusion, by enabling composition in the PSA Certified scheme and encouraging reuse across schemes we can make IoT security evaluation efficient for the electronics industry. At PSA Certified Level 1 we are making it easier for OEMs to demonstrate best practice security by design and consume the certificates from chip vendors and software platforms. Other schemes and cybersecurity baseline requirements are becoming aligned with the PSA Certified work providing even greater levels of efficiency.
For the chip vendor, we are providing a choice of two equivalent protection profiles and evaluation methodologies. The CSPN style PP is written in plain English and easier to interpret into good design choices. Choosing SESIP offers a more sophisticated EM with greater opportunities for the OEM to reuse the certificate if they wish to do their own SESIP evaluations at the device level.
Offering this choice to chip vendors (CSPN style PP or SESIP PP) will encourage more evaluations of the PSA-RoT and provide this valuable security component to the electronics industry which will ultimately make the IoT more secure.
